Cobalt Strikers
Cobalt Strike
Shop: @CobaltShopBot
All Projects: @MalwareLinks Связанные каналы | Похожие каналы
6 206
obunachilar
Kanalda mashhur
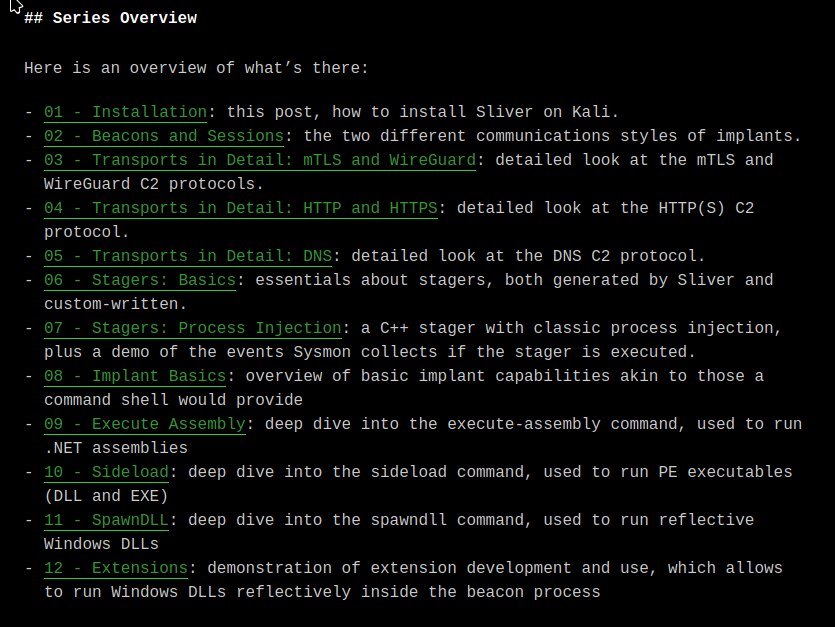
Сдаем экзамен по Sliver C2 framework https://dominicbreuker.com/post/learning_sliver_c2_01_inst...
NucleiScanner is a powerful automation tool for detecting unknown vulnerabilities in web applic...
Payload-Generator A script that can help automate the creation of payloads in Cobalt Strike. h...
Cobalt Strike Aggressor script for generating GadgetToJScript payloads. GadgetToJScript - This t...
Aaron Bushnell pro-palestine hackers are looking for professional defacers and exploiters for wid...



